Security
Table of Contents
Let`s be clear, nothing is 100% secured, but our built-in security is better and faster compared to the solution you were used before.
We use open source and commercial solutions to make strong and best practice security environment. Our security includes:
- Web Application Firewall tuned for WordPress
- Real-time malware detection
- DoS/DDoS protection
- Fully isolated per site environment
- Daily incremental backups
- Disaster backups
- Long-lived backups via CloudSnap
- Specially designed file system without write permissions to WordPress core files
- Hardened PHP
PHP code or a WordPress security plugin cannot act as a real security, Period. When it comes to pure security features, our built-in security is much more powerful, faster and everything in on the server level. All our sites hosted on Closte, including closte.com site does not use any WordPress security plugins.
However, some security plugins have advanced features like checking password strength, two-factor authorization, and similar features. For this use cases, you may want to use an extra security plugin if is compatible with our platform.
CloudFlare is a generic proxy that protects you just from very well known attacks as well DDOS. This doesn’t mean CloudFlare is bad service, but you need a Business plan with a custom WAF rules to meet the same protection as we are having. If you are that kind of big player, let us know.
On the other hand, thirty-party CDN/Proxy services are not compatible due to our built-in security.
A web application firewall (or WAF) filters, monitors, and blocks HTTP traffic to and from a website. By inspecting HTTP traffic, it can prevent attacks stemming from web application security flaws, such as SQL injection, cross-site scripting (XSS), file inclusion, and security misconfigurations.
A false-positive rule is a request blocked by our Web Application Firewall thinking it`s a hack attempt that causes a 403 response error.
Known false-positive rules:
- sending an image generated on a client-side e.g digital signature
- some WordPress builders also can produce false-positive rules
- A strange character in the post
We recommend to enable Development Mode in Closte plugin while developing but if you receive a 403 error on the production site, go to Site->Logs->Security tab and check if there are any security log with your IP address. Our system will also mark all IP addresses matching your current public IP address with a red color. If you find a blocked request with your IP and you believe it`s a false-positive rule, copy the ID of the rule, used to white-list the rule.
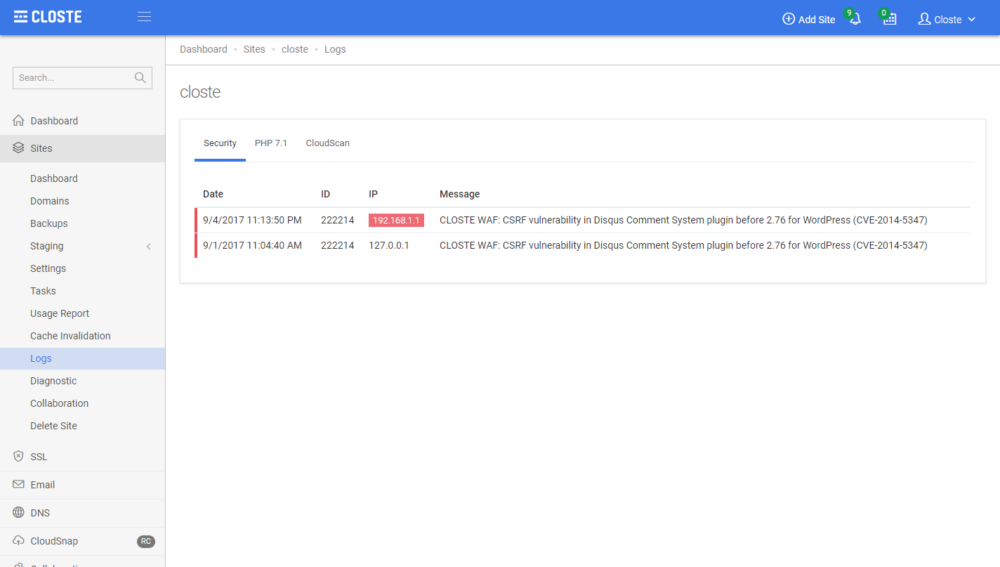
To white-list a false-positive rule, add the following content in the .htaccess file.
SecRuleRemoveById 1000
Where 1000 is the ID of a false-positive rule. You can also use advanced Apache rewrite conditions to make it even better.
<LocationMatch "^/comment/[0-9]+/approve$"> SecRuleRemoveById 1000 </LocationMatch>
For more information about Apache rewrite conditions, check their official documentation.
CloudScan is advanced, highly-efficient and real-time malware detection system tuned for WordPress.
To view the infected files, go to Site->Logs->CloudScan tab. Currently, there isn’t an option to view, modify or restore the file but we can help you, just open a support ticket.
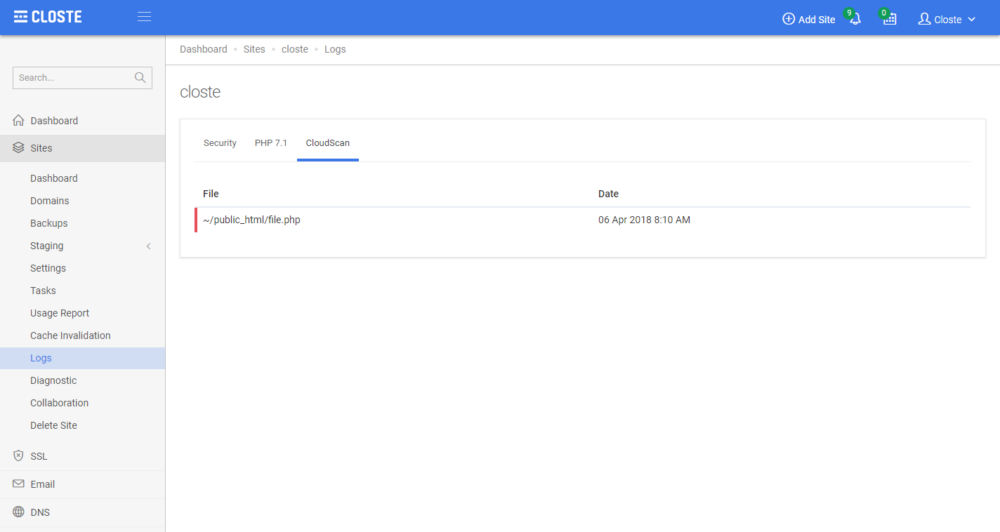
We plan to integrate several useful features that will help developers easily solve the problems via the Closte system. Here are some of the planned features:
- In-place file editing
- Restoration of file
- Soft manual scans
- Hard manual scans
- Whitelisting a file
- Blacklisting a file